Authentication Using RPCSEC_GSS
A determined snoop can overcome the authentication flavors mentioned previously- AUTH_SYS, AUTH_DES, and AUTH_KERB. For this reason a new networking layer, the Generic Security Standard API, or GSS-API, was added, which RPC programmers can use. The GSS-API framework offers two extra services beyond authentication: integrity and privacy.
Integrity. With the integrity service, the GSS-API uses the underlying mechanism to authenticate messages exchanged between programs. Cryptographic checksums establish:
The identity of the data originator to the recipient
The identity of the recipient to the originator if mutual authentication is requested
The authenticity of the transmitted data itself
Privacy. The privacy service includes the integrity service. In addition, the transmitted data is also encrypted to protect it from any eavesdroppers.
Because of U.S. export restrictions, the privacy service might not be available to all users.
Note - Currently, the GSS-API is exposed, and certain GSS-API features are visible through RPCSEC_GSS functions. See the GSS-API Programming Guide.
RPCSEC_GSS API
The RPCSEC_GSS security flavor enables ONC RPC applications to maximize the features of GSS-API. RPCSEC_GSS sits "on top" of the GSS-API layer as shown in the following figure.
Figure 5-1 GSS-API and RPCSEC_GSS Security Layers
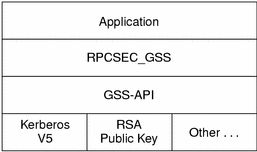
Using the programming interface for RPCSEC_GSS, ONC RPC applications can specify the following information:
Mechanism -- A security paradigm. Each kind of security mechanism offers a different kind of data protection, as well as one or more levels of data protection. You can use any security mechanism supported by the GSS-API (Kerberos V5, RSA public key, and so forth).
Security service -- Either privacy or integrity or neither. The default is integrity. The service is mechanism independent.
QOP -- Quality of protection. The QOP specifies the type of cryptographic algorithm to be used to implement privacy or integrity services. Each security mechanism can have one or more QOPs associated with it.
Applications can obtain lists of valid QOPs and mechanisms through functions provided by RPCSEC_GSS. See "Miscellaneous Functions". Developers should avoid hard-coding mechanisms and QOPs into their applications, so that the applications do not need to be modified to use new or different mechanisms and QOPs.
Note - Historically, "security flavor" and "authentication flavor" have had the same meaning. With the introduction of RPCSEC_GSS, "flavor" now has a somewhat different sense. A flavor can now include a service integrity or privacy along with authentication, although currently RPCSEC_GSS is the only flavor that falls into this category.
Using RPCSEC_GSS, ONC RPC applications establish a security context with a peer, exchange data, and destroy the context, just as they do with other flavors. After a context is established, the application can change the QOP and service for each data unit sent.
For more information on RPCSEC_GSS, including RPCSEC_GSS data types, see the rpcsec_gss(3N) man page.
RPCSEC_GSS Routines
The following table summarizes RPCSEC_GSS commands. It is a general overview of RPCSEC_GSS functions, rather than a specific description of each one. For more information on each function, see its man page, or check the rpcsec_gss(3NSL) man page for an overview, including a list of RPCSEC_GSS data structures.
Table 5-2 RPCSEC_GSS Functions
| Action | Function | Input | Output |
|---|---|---|---|
| Create a security context | rpc_gss_seccreate(3NSL) | CLIENT handle, principal name, mechanism, QOP, service type | AUTH handle |
| Change QOP, service type for context | rpc_gss_set_defaults(3NSL) | Old QOP, service | New QOP, service |
| Show maximum size for data before security transformation | rpc_gss_max_data_length(3NSL) (client side) | Maximum data size allowed by transport | Maximum pre-transformation data size |
| Show maximum size for data before security transformation | rpc_gss_svc_max_data_length(3NSL) (server side) | Maximum data size allowed by transport | Maximum pre-transformation data size |
| Set name of principals for server to represent | rpc_gss_set_svc_name(3NSL) | Principal name, RPC program, version #s | TRUE if successful |
| Fetch credentials of caller (client) | rpc_gss_getcred(3NSL) | Pointer to svc_req structure | UNIX credentials, RPCSEC_GSS credentials, cookie |
| Specify user-written callback function | rpc_gss_set_callback(3NSL) | Pointer to callback function | TRUE if successful |
| Create RPCSEC_GSS structure for principal names from unique parameters | rpc_gss_get_principal_name(3NSL) | Mechanism, user name, machine name, domain name | RPCSEC_GSS principal name structure |
| Fetch an error code when an RPCSEC_GSS routine fails | rpc_gss_get_error(3NSL) |
| RPCSEC_GSS error number, errno if applicable |
| Get strings for installed mechanisms | rpc_gss_get_mechanisms(3NSL) |
| List of valid mechanisms |
| Get valid QOP strings | rpc_gss_get_mech_info(3NSL) | Mechanism | Valid QOPs for that mechanism |
| Get the highest, lowest version numbers of RPCSEC_GSS supported | rpc_gss_get_versions(3NSL) |
| Highest, lowest versions |
| Check if a mechanism is installed | rpc_gss_is_installed(3NSL) | Mechanism | TRUE if installed |
| Convert ASCII mechanism to RPC object identifier | rpc_gss_mech_to_oid(3NSL) | Mechanism (as string) | Mechanism (as OID) |
| Convert ASCII QOP to integer | rpc_gss_qop_to_num(3NSL) | QOP (as string) | QOP (as integer) |
Creating a Context
You create contexts with the rpc_gss_seccreate() call. This function takes as its arguments:
A client handle returned, for example, by clnt_create()
The name of the server principal, for example, nfs@acme.com
The mechanism (for example, Kerberos V5) for the session
The security service type (for example, privacy)
The QOP for the session
Two GSS-API parameters that can remain opaque for most uses (that is, the programmer can supply NULL values)
This function returns an AUTH authentication handle. The following example shows how rpc_gss_seccreate() might be used to create a context using the Kerberos V5 security mechanism and the integrity service.
Example 5-10 rpc_gss_seccreate()
Note the following points about the example:
Although the mechanism was declared explicitly for ease of reading, it would be more commonly obtained programmatically with rpc_gss_get_mechanisms() from a table of available mechanisms.
The QOP is passed as a NULL, which sets the QOP to this mechanism's default. Otherwise, a valid value could, as with the mechanism, be obtained programmatically with rpc_gss_get_mechanisms(). See the rpc_gss_get_mechanisms(3NSL) man page for more information.
The security service type, rpc_gss_svc_integrity, is an enum of the RPCSEC_GSS type rpc_gss_service_t. rpc_gss_service_t has the following format:
typedef enum { rpc_gss_svc_default = 0, rpc_gss_svc_none = 1, rpc_gss_svc_integrity = 2, rpc_gss_svc_privacy = 3 } rpc_gss_service_t;The default security service maps to integrity, so the programmer could have specified rpc_gss_svc_default and obtained the same result.
For more information, see the rpc_gss_seccreate(3NSL) man page.