For More Chat Script Examples
A number of web sites offer sample chat scripts and assistance in creating them.
The PPP Frequently Asked Questions (FAQ) available from Australian National University posts URL.
Invoking the Chat Script
You call chat scripts by using the connect option. You can use connect "chat ..." in any PPP configuration file or on the command line.
Chat scripts are not executable, but the program that is invoked by connect must be executable. If you use the chat utility as that program and store your chat script in an external file by using the -f option, then your chat script file is not executable.
The chat program that is described in chat(1m) executes the actual chat script. The pppd daemon invokes the chat program whenever pppd encounters the connect "chat ..." option.
Note - You can use any external program, such as Perl or Tcl, to create advanced chat scripts. Solaris PPP 4.0 provides the chat utility as a convenience.
 How to Invoke a Chat Script (Task)
How to Invoke a Chat Script (Task)
Create the chat script as an ASCII file.
Invoke the chat script in any PPP configuration file by using the following syntax:
connect 'chat -f /etc/ppp/chatfile'
The -f flag indicates that a file name is to follow. /etc/ppp/chatfile represents the name of the chat file.
Give read permission for the external chat file to the user who will run the pppd command.
 Caution - The chat program always runs with the user's privileges, even
if the connect 'chat ...' option is invoked from a privileged
source. Thus, a separate chat file that is read with the -f
option must be readable by the invoking user. This privilege can be a security
problem if the chat script contains passwords or other sensitive information.
Caution - The chat program always runs with the user's privileges, even
if the connect 'chat ...' option is invoked from a privileged
source. Thus, a separate chat file that is read with the -f
option must be readable by the invoking user. This privilege can be a security
problem if the chat script contains passwords or other sensitive information.
Chat Script in an External File
If the chat script that is needed for a particular peer is long or complicated, consider creating the script as a separate file. External chat files are easy to maintain and document. You can add comments to the chat file by preceding them with the hash (#) sign.
The procedure "How to Create the Instructions for Calling a Peer" shows the use of a chat script that is contained in an external file.
Inline Chat Script
You can place the entire chat script conversation on a single line, similar to the following:
connect 'chat "" "AT&F1" OK ATDT5551212 CONNECT "\c"' |
Creating a Chat File That Is Executable
You can create a chat file that is an executable script to be run automatically when the dial-up link is initiated. Thus, you can run additional commands, such as stty for parity settings, besides those that are contained in a traditional chat script, during link initiation.
This executable chat script logs in to an old-style UNIX system that requires 7 bits/even parity and then changes to 8 bits/no parity when running PPP.
#!/bin/sh chat "" "AT&F1" OK "ATDT555-1212" CONNECT "\c" stty evenp chat ogin: pppuser ssword: "\q\U" % "exec pppd" stty -evenp |
 How to Create an Executable Chat Program
How to Create an Executable Chat Program
Use your text editor to create an executable chat program, such as the previous example.
Make the chat program executable.
# chmod +x /etc/ppp/chatprogram
Invoke the chat program.
connect /etc/ppp/chatprogram
Chat programs do not have to be located within the /etc/ppp file system. You can store them in any location.
Authenticating Callers on a Link
This section explains how the PPP authentication protocols work and explains the databases that are associated with them.
Password Authentication Protocol (PAP)
PAP authentication is somewhat similar in operation to the UNIX login program, though it does not grant shell access to the user. PAP uses the PPP configuration files and PAP database in the form of the /etc/ppp/pap-secrets file for setting up authentication and defining PAP security credentials. These credentials include a peer name (a "user name" in PAP parlance), password, and related information for each caller who is permitted to link to the local machine. The PAP user names and passwords can be identical to or different from the UNIX user names and passwords in the password database.
/etc/ppp/pap-secrets File
The PAP database is implemented in the /etc/ppp/pap-secrets file. Machines on both sides of the PPP link must have properly configured PAP credentials in their /etc/ppp/pap-secrets files for successful authentication. The caller (authenticatee) supplies credentials in the user and password columns of the /etc/ppp/pap-secrets file or in the obsolete +ua file. The server (authenticator) validates these credentials against information in /etc/ppp/pap-secrets, through the UNIX passwd database, or the PAM facility.
The /etc/ppp/pap-secrets file has the following syntax.
Table 36-5 Syntax of /etc/ppp/pap-secrets
Caller | Server | Password | IP Addresses |
|---|---|---|---|
myclient | ISP-server | mypassword | * |
The parameters have the following meaning:
myclient | PAP user name of the caller. Often this name is identical to the caller's UNIX user name, particularly if the dial-in server uses the login option of PAP. |
ISP-server | Name of the remote machine, often a dial-in server. |
mypassword | Caller's PAP password. |
IP address | IP address that is associated with the caller. Use an asterisk (*) to indicate any IP address. |
Creating PAP Passwords
PAP passwords are sent over the link in the clear (in readable ASCII format). For the caller (authenticatee), the PAP password must be stored in the clear in any of the following locations:
In /etc/ppp/pap-secrets
In another external file
In a named pipe through the pap-secrets @ feature
As an option to pppd, either on the command line or in a PPP configuration file
Through the +ua file
On the server (authenticator), the PAP password can be hidden by doing one of the following:
Specifying papcrypt and using passwords that are hashed by crypt(3C) in the pap-secrets file.
Specifying the login option to pppd and omitting the password from the pap-secrets file by placing double quotes ("") in the password column. In this instance, authentication is done through the UNIX passwd database or the pam(3pam) mechanism.
What Happens During PAP Authentication
PAP authentication occurs in the following sequence.
Figure 36-1 PAP Authentication Process
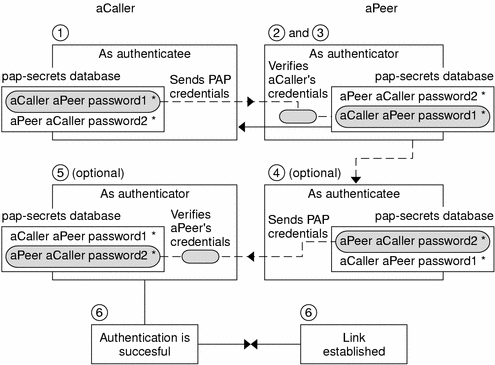
The caller (authenticatee) calls the remote peer (authenticator) and provides its PAP user name and password as part of link negotiation.
The peer verifies the identity of the caller in its/etc/ppp/pap-secrets file. If the peer uses the login option of PAP, it verifies the caller's user name and password in its password database.
If authentication is successful, the peer continues link negotiation with the caller. If authentication fails, the link is dropped.
(Optional) If the caller authenticates responses from remote peers, the remote peer must send its own PAP credentials to the caller. Thus, the remote peer becomes the authenticatee and the caller the authenticator.
The original caller reads its own /etc/ppp/pap-secrets to verify the identity of the remote peer.
Note - If the original caller does require authentication credentials from the remote peer, Step 1 and Step 4 happen in parallel.
If the peer is authenticated, negotiation continues. Otherwise, the link is dropped.
Negotiation between caller and peer continues until the link is successfully established.