Using the login Option With /etc/ppp/pap-secrets
You can add the login option for authenticating PAP credentials to any PPP configuration file. When login is specified, for example, in /etc/ppp/options, pppd verifies that the caller's PAP credentials exist in the Solaris password database. The following table shows the format of a /etc/ppp/pap-secrets file with the login option.
Table 36-6 /etc/ppp/pap-secrets With login Option
Caller | Server | Password | IP Addresses |
|---|---|---|---|
joe | * | " " | * |
sally | * | " " | * |
sue | * | " " | * |
The parameters have the following meanings:
Caller | Names of all authorized callers. |
Server | Asterisk, which indicates that any server name is valid. The name option is not required in the PPP configuration files. |
Password | Double quotes, which indicate that any password is valid. If you type a password in this column, then the password that is supplied by the peer must match both the PAP password and the UNIX passwd database. |
IP Addresses | Asterisk, which indicates that any IP address is allowed. |
Challenge-Handshake Authentication Protocol (CHAP)
CHAP authentication uses the notion of the challenge and response, which means that the peer (authenticator) challenges the caller (authenticatee) to prove its identity. The challenge includes a random number and a unique ID that is generated by the authenticator. The caller must use the ID, random number, and its CHAP security credentials to generate the proper response (handshake) to send to the peer.
CHAP security credentials include a CHAP user name and a CHAP secret, an arbitrary string that is known to both caller and peer before they negotiate a PPP link. You configure CHAP security credentials in the CHAP database, /etc/ppp/chap-secrets.
/etc/ppp/chap-secrets File
The CHAP database is implemented in the /etc/ppp/chap-secrets file. Machines on both sides of the PPP link must have each others' CHAP credentials in their /etc/ppp/chap-secrets files for successful authentication.
Note - Unlike PAP, the shared secret must be in the clear on both peers. You cannot use crypt, PAM, or the PPP login option with CHAP.
The /etc/ppp/chap-secrets file has the following syntax.
Table 36-7 Syntax of /etc/ppp/chap-secrets
Caller | Server | CHAP secret | IP Addresses |
|---|---|---|---|
myclient | myserver | secret5748 | * |
The parameters have the following meanings:
myclient | CHAP user name of the caller. This name can be the same or different from the caller's UNIX user name. |
myserver | Name of the remote machine, often a dial-in server. |
secret5748 | Caller's CHAP secret. Note - Unlike PAP passwords, CHAP secrets are never sent over the link. Rather, they are used when the local machines compute the response. |
IP address | IP address that is associated with the caller. Use an asterisk (*) to indicate any IP address. |
What Happens During CHAP Authentication
CHAP authentication occurs in the following sequence.
Figure 36-2 CHAP Authentication Sequence
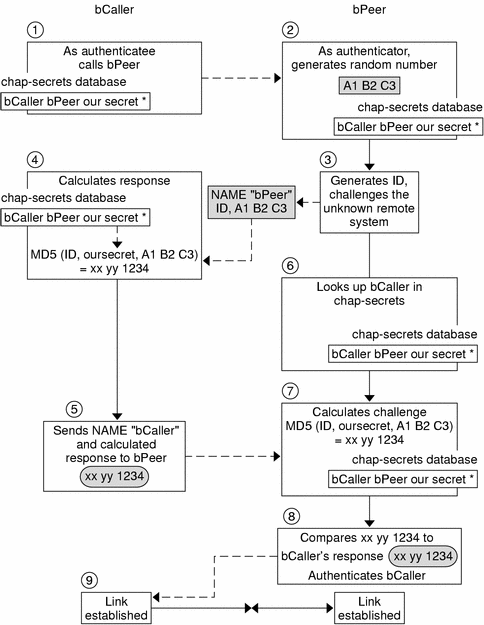
Two peers that are about to initiate communications agree on a secret to be used for authentication during negotiation of a PPP link.
The administrators of both machines add the secret, CHAP user names, and other CHAP credentials to the /etc/ppp/chap-secrets database of their respective machines.
The caller (authenticatee) calls the remote peer (authenticator).
The authenticator generates a random number and an ID, and sends them to the authenticatee as a challenge.
The authenticatee looks up the peer's name and secret in its /etc/ppp/chap-secrets database.
The authenticatee calculates a response by applying the MD5 computational algorithm to the secret and the peer's random number challenge. Then the authenticatee sends the results as its response to the authenticator.
The authenticator looks up the authenticatee's name and secret in its /etc/ppp/chap-secrets database.
The authenticator calculates its own figure by applying MD5 to the number that was generated as the challenge and the secret for the authenticatee in /etc/ppp/chap-secrets.
The authenticator compares its results with the response from the caller. If the two numbers are the same, the peer has successfully authenticated the caller, and link negotiation continues. Otherwise the link is dropped.
Creating an IP Addressing Scheme for Callers
Consider creating one or more IP addresses for all incoming calls instead of assigning a unique IP address to each remote user. Dedicated IP addresses are particularly important if the number of potential callers exceeds the number of serial ports and modems on the dial-in server. You can implement a number of different scenarios, depending on your site's needs. Moreover, the scenarios are not mutually exclusive.
Assigning Dynamic IP Addresses to Callers
Dynamic addressing involves the assignment to each caller of the IP address that is defined in /etc/ppp/options.ttyname. Dynamic addressing occurs on a per-serial port basis. Each time a call arrives over a particular serial line, the caller is given the IP address that is defined in the /etc/ppp/options.ttyname file for the serial interface that is handling the call.
For example, suppose a dial-in server has four serial interfaces that provide dial-up service to incoming calls:
For serial port term/a, create the file /etc/ppp/options.term.a with the following entry:
:10.1.1.1
For serial port term/b, create the file /etc/ppp/options.term.b with the following entry:
:10.1.1.2
For serial port term/c, create the file /etc/ppp/options.term.c with the following entry:
:10.1.1.3
For serial port term/d, create the file /etc/ppp/options.term.d with the following entry:
:10.1.1.4
The advantages of dynamic addressing include the following:
You can track PPP network usage down to the serial port.
You can assign a minimum number of IP addresses for PPP use.
You can administer IP filtering in a more simplified fashion.
Assigning Static IP Addresses to Callers
If your site implements PPP authentication, you can assign specific, static IP addresses to individual callers. In this scenario, every time a dial-out machine calls the dial-in server, the caller receives the same IP address.
You implement static addresses in either the pap-secrets or chap-secrets database. Here is a sample /etc/ppp/pap-secrets file with static IP addresses defined.
Caller | Server | Password | IP Addresses |
|---|---|---|---|
joe | myserver | joepasswd | 10.10.111.240 |
sally | myserver | sallypasswd | 10.10.111.241 |
sue | myserver | suepasswd | 10.10.111.242 |
Here is a sample /etc/ppp/chap-secrets file that defines static IP addresses.
Caller | Server | CHAP secret | IP Addresses |
|---|---|---|---|
account1 | myserver | secret5748 | 10.10.111.244 |
account2 | myserver | secret91011 | 10.10.111.245 |