| lowerable | Superuser privileges are not required to lower the privileged values for this control. |
| no-deny | Even when threshold values are exceeded, access to the resource is never denied. |
| cpu-time | SIGXCPU is available to be sent when threshold values of this resource are reached. |
| inf | Any value with RCTL_LOCAL_MAXIMAL defined actually represents an infinite quantity, and the value is never enforced. |
Use prctl to display local values and actions for the resource control.
$ prctl -n process.max-cpu-time $$ 353939: -ksh process.max-cpu-time [ lowerable no-deny cpu-time inf ] 18446744073709551615 privileged signal=XCPU [ max ] 18446744073709551615 system deny [ max ] |
The max (RCTL_LOCAL_MAXIMAL) flag is set for both threshold values, and the inf (RCTL_GLOBAL_INFINITE) flag is defined for this resource control. Hence, as configured, both threshold quantities represent infinite values and they are never exceeded.
Resource Control Enforcement
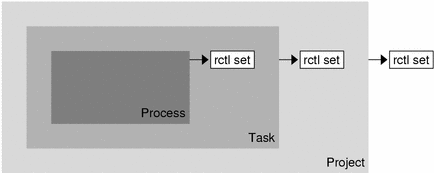
More than one resource control can exist on a resource, one at each containment level in the process model. If resource controls are active on the same resource at different container levels, the smallest container's control is enforced first. Thus, action is taken on process.max-cpu-time before task.max-cpu-time if both controls are encountered simultaneously.
Figure 8-1 Process Collectives, Container Relationships, and Their Resource Control Sets
Global Monitoring of Resource Control Events
In situations where the resource consumption of processes is unknown, you can use the global resource control actions available with rctladm(1M). For example, consider a syslog action has been established on a resource control. Any encounter of a threshold value by any entity managed by that resource control results in a system message being logged at the configured logging level.
Configuration
Each resource control that is listed in Table 8-1 can be assigned to a project at login or when newtask(1) or the other project-aware launchers at(1), batch (see at(1)), or cron(1M) are invoked. Each command that is initiated is launched in a separate task with the invoking user's default project.
Updates to entries in the project database, whether to the /etc/project file or to a representation of the database in a network name service, are not applied to currently active projects. The updates are applied when a new task joins the project through login(1) or newtask.
Temporarily Updating Resource Control Values on a Running System
Values that are changed in the project database only become effective for new tasks that are started in a project. However, you can use the rctladm and prctl commands to update resource controls on a running system.
Updating Logging Status
The rctladm command affects the global logging state of each resource control on a system-wide basis. This command can be used to view the global state and to set up the level of syslog logging when controls are exceeded.
Updating Resource Controls
You can view and temporarily alter resource control values and actions on a per-process, per-task, or per-project basis by using prctl. A project, task, or process ID is given as input, and the command operates on the resource control at the level where it is defined.
Any modifications to values and actions become effective immediately. However, these modifications apply to the current session only. The changes are not recorded in the project database. If the system is restarted, the modifications are lost. Permanent changes to resource controls must be made in the project database.
All resource control settings that can be modified in the project database can also be modified with the prctl command. Both basic and privileged values can be added or deleted and their actions can be modified. By default, the basic type is assumed for all set operations, but processes and users with superuser privileges can also modify privileged resource controls. System resource controls cannot be altered.
Using Resource Controls
 How to Set the Maximum Number of LWPs for Each Task in a Project
How to Set the Maximum Number of LWPs for Each Task in a Project
Type this entry in the /etc/project database to set the maximum number of LWPs in each task in project x-files to 3.
x-files:100::root::task.max-lwps=(privileged,3,deny) |
When superuser creates a new task in project x-files by joining it with newtask, superuser cannot create more than three LWPs while running in this task, as shown in the following annotated sample session.
# newtask -p x-files csh
# prctl -n task.max-lwps $$
688: csh
task.max-lwps
3 privileged deny
2147483647 system deny
# id -p
uid=0(root) gid=1(other) projid=100(x-files)
# ps -o project,taskid -p $$
PROJECT TASKID
x-files 236
# csh /* creates second LWP */
# csh /* creates third LWP */
# csh /* cannot create more LWPs */
Vfork failed
#
|
 How to Set Multiple Controls on a Project
How to Set Multiple Controls on a Project
The /etc/project file can contain settings for multiple resource controls for each project as well as multiple threshold values for each control. Threshold values are defined in action clauses, which are comma-separated for multiple values.
The following line in the file sets a basic control with no action on the maximum LWPs per task for project x-files. The line also sets a privileged deny control on the maximum LWPs per task. This control causes any LWP creation that exceeds the maximum to fail, as shown in the previous example. Finally, the maximum file descriptors per process are limited at the basic level, which forces failure of any open call that exceeds the maximum.
x-files:101::root::task.max-lwps=(basic,10,none),(privileged,500,deny);
process.max-file-descriptor=(basic,128,deny)
|
 How to Use prctl
How to Use prctl
As superuser, type prctl to display the maximum file descriptor for the current shell that is running:
# prctl -n process.max-file-descriptor $$
8437: sh
process.max-file-descriptor [ lowerable deny ]
256 basic deny
65536 privileged deny
2147483647 system deny
|
Use the prctl command to temporarily add a new privileged value to deny the use of more than three LWPs per task for the x-files project. The result is identical to the result in "How to Set the Maximum Number of LWPs for Each Task in a Project", as shown in the following annotated sample session:
# newtask -p x-files
# id -p
uid=0(root) gid=1(other) projid=101(x-files)
# prctl -n task.max-lwps -t privileged -v 3 -e deny -i project x-files
# prctl -n task.max-lwps -i project x-files
670: sh
task.max-lwps
3 privileged deny
2147483647 system deny
|
You can also use prctl -r to change the lowest value of a resource control.
# prctl -n process.max-file-descriptor -r -v 128 $$ |
 How to Use rctladm
How to Use rctladm
You can use rctladm to enable the global syslog attribute of a resource control. When the control is exceeded, notification is logged at the specified syslog level. Type the following:
# rctladm -e syslog process.max-file-descriptor |
Capacity Warnings
A global action on a resource control enables you to receive notice of any entity that is tripping over a resource control value.
For example, assume you want to determine whether a web server possesses sufficient CPUs for its typical workload. You could determine this capacity by analyzing sar(1) data for idle CPU time and load average. Alternately, you could examine extended accounting data to determine the number of simultaneous processes that are running for the web server process.
However, an easier method is to place the web server in a task. Then set a global action, using syslog, to notify you whenever a task exceeds a scheduled number of LWPs appropriate for the machine's capabilities.