 How to Log In to Another Host with Secure Shell
How to Log In to Another Host with Secure Shell
Use the ssh command, specifying the name of the remote host.
The first time you run ssh, a prompt questions the authenticity of the remote host, as follows.myLocalHost% ssh myRemoteHost
The authenticity of host 'myRemoteHost' can't be established. RSA key fingerprint in md5 is: 04:9f:bd:fc:3d:3e:d2:e7:49:fd:6e:18:4f:9c:26 Are you sure you want to continue connecting(yes/no)?
This prompt is normal, and you should type yes and continue. If you have used ssh in the past on this remote host and this warning message still appears, then there might be a breach in your security.
Enter the Secure Shell passphrase and the account password when you are prompted for them.
Enter passphrase for key '/home/johndoe/.ssh/id_rsa': <Return> johndoe@myRemoteHost's password: <Return> Last login: Fri Jul 20 14:24:10 2001 from myLocalHost myRemoteHost%
Conduct any transactions on the remote host. Any commands that you send and any responses that are received are encrypted.
Note - If you wish to subsequently change your passphrase, use ssh-keygen with the -p option.
When you are finished with your remote session, type exit or use your usual method for exiting your shell.
myRemoteHost% exit myRemoteHost% logout Connection to myRemoteHost closed myLocalHost%
 How to Log in With No Password While Using ssh-agent
How to Log in With No Password While Using ssh-agent
If you want to omit passphrase and password entry when you are using Secure Shell, you can use the agent daemon. Use the ssh-agent command at the beginning of the session. Then, store your private keys with the agent by using ssh-add. If you have different accounts on different hosts, add those keys that you intend to use in the session. You can start the agent manually when needed as described in the following procedure. Or, you can set the agent to run automatically at the start of every session as described in "How to Set ssh-agent to Run Automatically".
Start the agent daemon.
The ssh-agent command starts the agent daemon and displays its process ID.
myLocalHost% eval `ssh-agent` Agent pid 9892 myLocalHost%
Add your private key to the agent daemon.
The ssh-add command adds your private key to the agent daemon so that subsequent Secure Shell activity will not prompt you for the passphrase.
myLocalHost% ssh-add Enter passphrase for /home/johndoe/.ssh/id_rsa: Identity added: /home/johndoe/.ssh/id_rsa(/home/johndoe/.ssh/id_rsa) myLocalHost%
Start a Secure Shell session.
myLocalHost% ssh myRemoteHost
Example--Using ssh-add Options
You can use ssh-add to add other keys to the daemon as well. For example, you might concurrently have DSA v2, RSA v2, and RSA v1 keys. To list all keys that are stored in the daemon, use the -l option. To delete a single key from the daemon, use the -d option. To delete all keys, use the -D option.
myLocalHost% eval `ssh-agent` Agent pid 3347 myLocalHost% ssh-add Enter passphrase for /home/johndoe/.ssh/id_rsa: Identity added: /home/johndoe/.ssh/id_rsa(/home/johndoe/.ssh/id_rsa) myLocalHost% ssh-add /home/johndoe/.ssh/id_dsa Enter passphrase for /home/johndoe/.ssh/id_dsa: <type passphrase> Identity added: /home/johndoe/.ssh/id_dsa(/home/johndoe/.ssh/id_dsa) myLocalHost% ssh-add -l md5 1024 0e:fb:3d:53:71:77:bf:57:b8:eb:f7:a7:aa:df:e0:d1 /home/johndoe/.ssh/id_rsa(RSA) md5 1024 c1:d3:21:5e:40:60:c5:73:d8:87:09:3a:fa:5f:32:53 /home/johndoe/.ssh/id_dsa(DSA) myLocalHost% ssh-add -d Identity removed: /home/johndoe/.ssh/id_rsa(/home/johndoe/.ssh/id_rsa.pub) /home/johndoe/.ssh/id_dsa(DSA) |
 How to Set ssh-agent to Run Automatically
How to Set ssh-agent to Run Automatically
If you want to avoid providing your passphrase and password whenever you use Secure Shell, you can start an agent daemon (ssh-agent) by using the .dtprofile script.
To start the agent daemon automatically, add the following lines to the end of the $HOME/.dtprofile script:
if [ "$SSH_AUTH_SOCK" = "" -a -x /usr/bin/ssh-agent ]; then eval `/usr/bin/ssh-agent` fiTo terminate the Secure Shell agent daemon when you exit the CDE session, add the following to the $HOME/.dt/sessions/sessionexit script:
if [ "$SSH_AGENT_PID" != "" -a -x /usr/bin/ssh-agent ]; then /usr/bin/ssh-agent -k fiThis entry ensures that no one can use the Secure Shell agent after the CDE session is terminated.
Start a Secure Shell session.
myLocalHost% ssh myRemoteHost
There is no prompt for a passphrase.
 How to Use Secure Shell Port Forwarding
How to Use Secure Shell Port Forwarding
You can specify a local port to be forwarded to a remote host. Effectively, a socket is allocated to listen to the port on the local side. The connection from this port is made over a secure channel to the remote host. For example, you might specify port 143 to obtain email remotely with IMAP4. Similarly, a port can be specified on the remote side.
To set a local port to be forwarded, specify the local port to listen to, and the remote host and port to forward to.
myLocalHost% ssh -L localPort:remoteHost:remotePort
To set a remote port to receive a secure connection, specify the remote port to listen to, and the local host and port to forward to.
myLocalHost% ssh -R remotePort:localHost:localPort
Example -- Using Local Port Forwarding to Receive Mail
The following example demonstrates how you can use local port forwarding to receive mail securely from a remote server.
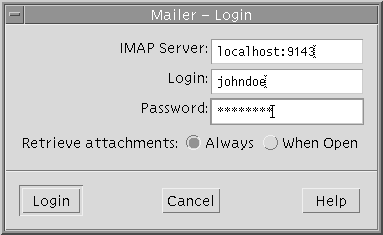
myLocalHost% ssh -L 9143:myRemoteHost:143 myRemoteHost |
This command forwards connections to port 9143 on myLocalHost to port 143 (the IMAP v2 server port) on myRemoteHost. When the user launches a mail application, he or she needs to specify the local port number. An example that uses the dtmail command is shown in Figure 4-1.
Note that the term localhost in this case and in "Example -- Using Remote Port Forwarding to Communicate Outside of a Firewall" refers to the keyword that designates the user's local host. localhost should not be confused with myLocalHost, the hypothetical host name that is used to identify a local host in the examples in this chapter.
Figure 4-1 Specifying Port Forwarding for Email
Example -- Using Remote Port Forwarding to Communicate Outside of a Firewall
This example demonstrates how a user in an enterprise environment can forward connections from a host on an external network to a host inside a corporate firewall.
myLocalHost% ssh -R 9022:myLocalHost:22 myOutsideHost |
This command forwards connections to port 9022 on myOutsideHost to port 22 (the sshd server) on the local host.
myOutsideHost% ssh -p 9022 localhost myLocalHost% |
This command demonstrates how after the remote forwarding connection has been established, the user can use ssh to connect securely from the remote host.




