Realms
A realm is a logical network, similar to a domain, which defines a group of systems under the same master KDC. Figure 6-3 shows how realms can relate to one another. Some realms are hierarchical (one realm being a superset of the other realm). Otherwise, the realms are non-hierarchical (or "direct") and the mapping between the two realms must be defined. A feature of SEAM is that it permits authentication across realms. Each realm only needs to have a principal entry for the other realm in its KDC. The feature is called cross-realm authentication.
Figure 6-3 Realms
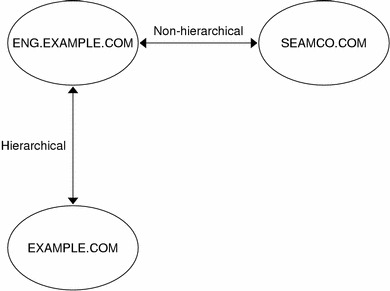
Realms and Servers
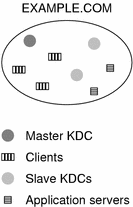
Each realm must include a server that maintains the master copy of the principal database. This server is called the master KDC server. Additionally, each realm should contain at least one slave KDC server, which contains duplicate copies of the principal database. Both the master KDC server and the slave KDC server create tickets that are used to establish authentication.
Realms can also include NFS servers, which provide NFS services by using Kerberos authentication. If you have installed SEAM 1.0 or 1.0.1, the realm might include a SEAM network application server, which provides access to Kerberized applications (such as ftp, telnet, and rsh).
The following figure shows what a hypothetical realm might contain.
Figure 6-4 A Typical Realm
SEAM Security Services
In addition to providing secure authentication of users, SEAM provides two security services:
Integrity - Just as authentication ensures that clients on a network are who they claim to be, integrity ensures that the data they send is valid and has not been tampered with during transit. Integrity is done through cryptographic checksumming of the data. Integrity also includes user authentication.
Privacy - Privacy takes security a step further. Privacy not only includes verifying the integrity of transmitted data, but it encrypts the data before transmission, protecting it from eavesdroppers. Privacy authenticates users, as well.
SEAM Releases
Components of the SEAM product have been included in four releases. The following table describes which components are included in each release. All components are described in the following sections.
Table 6-1 SEAM Release Contents
Release Name | Contents |
|---|---|
SEAM 1.0 in Solaris Easy Access Server (SEAS) 3.0 | Full release of SEAM for the Solaris 2.6 and 7 releases |
SEAM in the Solaris 8 release | SEAM client software only |
SEAM 1.0.1 in the Solaris 8 Admin Pack | SEAM KDC and remote applications for the Solaris 8 release |
SEAM in the Solaris 9 release | SEAM KDC and client software only |
SEAM 1.0 Components
Similar to the MIT distribution of Kerberos V5, SEAM includes the following:
Key Distribution Center (KDC) (master):
Kerberos database administration daemon - kadmind
Kerberos ticket processing daemon - krb5kdc
Slave KDCs
Database administration programs - kadmin and kadmin.local
Database propagation software - kprop
User programs for obtaining, viewing, and destroying tickets - kinit, klist, kdestroy - and for changing your SEAM password - kpasswd
Applications - ftp, rcp, rlogin, rsh, and telnet - and daemons for these applications - ftpd, rlogind, rshd and telnetd
Administration utilities - ktutil, kdb5_util
Several libraries
In addition, SEAM includes the following:
SEAM Administration Tool (gkadmin) - Allows you to administer the KDC. This Java™ technology-based GUI allows an administrator to perform the tasks that are usually performed through the kadmin command.
The Pluggable Authentication Module (PAM) - Allows applications to use various authentication mechanisms. PAM can be used to make login and logouts transparent to the user.
A utility (gsscred) and a daemon (gssd) - These programs help map UNIX user IDs (UIDs) to principal names. These programs are needed because SEAM NFS servers use UNIX UIDs to identify users and not principal names, which are stored in a different format.
The Generic Security Service Application Programming Interface (GSS-API) - Allows applications to use multiple security mechanisms without having to recompile the application every time a new mechanism is added. Because GSS-API is machine-independent, it is appropriate for applications on the Internet. GSS-API provides applications with the ability to include the integrity and privacy security services, as well as authentication.
The RPCSEC_GSS Application Programming Interface (API) - Allows NFS services to use Kerberos authentication. RPCSEC_GSS is a new security flavor that provides security services that are independent of the mechanisms being used. RPCSEC_GSS sits "on top" of the GSS-API layer. Any pluggable GSS_API-based security mechanism can be used by applications that use RPCSEC_GSS.
A preconfiguration procedure - Allows you to set the parameters for installing and configuring SEAM, which make SEAM installation automatic. This procedure is especially useful for multiple installations.
Kernel modifications - Allows for faster performance.
SEAM Components in the Solaris 8 Release
The Solaris 8 release included only the client-side portions of SEAM, so many components are not included. This product enables systems that run the Solaris 8 release to become SEAM clients without having to install SEAM separately. To use these capabilities, you must install a KDC that uses either SEAS 3.0 or the Solaris 8 Admin Pack, the MIT distribution, or Windows2000. The client-side components are not useful without a configured KDC to distribute tickets. The following components were included in this release:
User programs for obtaining, viewing, and destroying tickets - kinit, klist, kdestroy.
User program for changing your SEAM password - kpasswd.
Key table administration utility - ktutil.
Additions to the Pluggable Authentication Module (PAM) - Allows applications to use various authentication mechanisms. PAM can be used to make login and logouts transparent to the user.
GSS_API plug-ins - Provides Kerberos protocol and cryptographic support.
NFS client and server support.




