System Configuration Files Check
During this task, ASET checks various system tables, most of which are in the /etc directory. These files are the following:
/etc/default/login
/etc/hosts.equiv
/etc/inetd.conf
/etc/aliases
/var/adm/utmpx
/.rhosts
/etc/vfstab
/etc/dfs/dfstab
/etc/ftpd/ftpusers
ASET performs various checks and modifications on these files, and reports all problems in the sysconf.rpt file.
Environment Variables Check
This task checks how the PATH and UMASK environment variables are set for root, and other users, in the /.profile, /.login, and /.cshrc files.
The results of checking the environment for security are reported in the env.rpt file.
eeprom Check
This task checks the value of the eeprom security parameter to ensure that it is set to the appropriate security level. You can set the eeprom security parameter to none, command, or full.
ASET does not change this setting, but reports its recommendations in the eeprom.rpt file.
Firewall Setup
This task ensures that the system can be safely used as a network relay. This task protects an internal network from external public networks by setting up a dedicated system as a firewall, which is described in "Firewall Systems". The firewall system separates two networks. In this situation, each network approaches the other network as untrusted. The firewall setup task disables the forwarding of Internet Protocol (IP) packets and hides routing information from the external network.
The firewall task runs at all security levels, but takes action only at the highest level. If you want to run ASET at high security, but find that your system does not require firewall protection, you can eliminate the firewall task by editing the asetenv file.
Any changes that are made are reported in the firewall.rpt file.
ASET Execution Log
ASET generates an execution log whether it runs interactively or in the background. By default, ASET generates the log file on standard output. The execution log confirms that ASET ran at the designated time, and also contains any execution error messages. The aset -n command directs the log to be delivered by electronic mail to a designated user. For a complete list of ASET options, refer to the aset(1M) man page.
Example of an ASET Execution Log File
ASET running at security level low
Machine=example; Current time = 0325_08:00
aset: Using /usr/aset as working directory
Executing task list...
firewall
env
sysconfig
usrgrp
tune
cklist
eeprom
All tasks executed. Some background tasks may still be running.
Run /usr/aset/util/taskstat to check their status:
$/usr/aset/util/taskstat aset_dir
Where aset_dir is ASET's operating directory, currently=/usr/aset
When the tasks complete, the reports can be found in:
/usr/aset/reports/latest/*.rpt
You can view them by:
more /usr/aset/reports/latest/*.rpt
|
The execution log first shows the system and time that ASET was run. Then, the execution log lists each task as it is started.
ASET invokes a background process for each of these tasks, which are described in "ASET Tasks". The task is listed in the execution log when it starts. This listing does not indicate that it has been completed. To check the status of the background tasks, use the taskstat command.
ASET Reports
All report files that are generated from ASET tasks are stored in subdirectories under the /usr/aset/reports directory. This section describes the structure of the /usr/aset/reports directory, and provides guidelines on managing the report files.
ASET places the report files in subdirectories that are named to reflect the time and date when the reports are generated. This convention enables you to keep an orderly trail of records that document the system status as it varies between ASET executions. You can monitor and compare these reports to determine the soundness of your system's security.
The following figure shows an example of the reports directory structure.
Figure 20-1 Structure of the ASET reports Directory
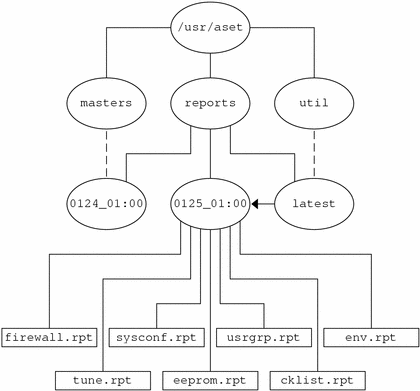
This example shows two report subdirectories.
0124_01:00
0125_01:00
The subdirectory names indicate the date and time that the reports were generated. Each report subdirectory name has the following format:
monthdate_hour:minute
where month, date, hour, and minute are all two-digit numbers. For example, 0125_01:00 represents January 25, at 1 a.m.
Each of the two report subdirectories contains a collection of reports that are generated from one execution of ASET.
The latest directory is a symbolic link that always points to the subdirectory that contains the latest reports. Therefore, to look at the latest reports that ASET has generated, you can go to the /usr/aset/reports/latest directory. There is a report file in this directory for each task that ASET performed during its most recent execution.




